Openvpn Hardware Query,Yost Woodworking Vise Installation Years,Underdrawers Meaning In English,Easy Pallet Wood Projects Diy 400 - Step 1
06.01.2021This section describes all of the available options with OpenVPN and when they are typically used. Subsequent sections cover examples of configuring site-to-site and remote access VPNs with OpenVPN, using the most common options and a minimal configuration.
Check this box and click Save to retain the configuration, but not enable the server. Any other active servers are unaffected. This is the role for the server, which specifies how routers or users will connect to this server instance. Changing this will also affect what options will appear on the rest of the page, so only relevant choices are displayed. This choice offers increased security as well as the ability for the server to push configuration commands to the remote peer router when using a openvpn hardware query style setup.
Remote peer routers can also have certificates revoked to remove access if they become compromised. A connection between local and remote networks that is secured by a single Shared Key configured on both nodes. This choice is easier to openvpn hardware query, but is less secure. If a shared key is compromised, a new key must be generated and then copied to any router or client using the old shared key. In this openvpn hardware query, a separate server instance is needed for each client.
This choice is a mobile client setup with per-user X. Mobile clients can also have keys revoked to remove access if a key is compromised, such as a stolen or misplaced laptop. A client access server that does not use certificates, but does require the end user to supply a username and password when making a connection.
The most secure choice offered. Client access can be removed not only by revoking the certificate, but also by changing the password. Also, if a compromised key is not immediately discovered, the danger is lessened because it is unlikely that the attacker openvpn hardware query the keys and the password. When using the OpenVPN wizard, this is the mode which is configured during that process. Connectionless protocols such as UDP are always preferable when tunneling traffic.
TCP is connection oriented with guaranteed delivery, so any lost packets are retransmitted. This sounds like a good idea on the surface but TCP retransmissions will cause performance to degrade significantly on heavily loaded Internet connections or those with consistent packet loss.
TCP traffic frequently exists within tunnels and it is undesirable to retransmit lost packets of encapsulated VPN traffic. Infrequent occurrences of this will be unnoticeable but recurring loss will cause significantly lower performance openvpn hardware query UDP.
If the traffic inside the tunnel requires reliable delivery, it will be using a protocol such as TCP which ensures that and will handle its own retransmissions. Not all clients support tap mode, using tun is more stable and more widely supported. Specifically, clients such as those found on Android and iOS only support tun mode in the Apps most people can use. Some Android and iOS OpenVPN apps that require rooting or jailbreaking a device do support tap, but the consequences of doing so can be a bit too high for most users.
This also controls which interface the traffic from the server will exit. Several types of options are listed in the drop-down for Interfaceand some have special behavior or use cases:. OpenVPN will bind to the interface address. For use with failover groups, OpenVPN will bind to the address of the interface that is currently active in the group. Openvpn hardware query that interface gateway becomes unreachable, the next one will be used instead, and so on.
Binds to every address on every interface. Though tempting, this option is not recommended. The local port is the port number OpenVPN will use to listen. Firewall rules need to allow traffic to this port and it must be specified in the client configuration.
The port for each server must be unique for each interface. When using a shared key instance, either check the Automatically generate a shared key box to make a new key, or uncheck the box to paste in a shared key from an existing OpenVPN tunnel.
When generating the key automatically, return to the edit screen for this tunnel later to obtain the key which may be copied to the remote router. TLS, or Transport Layer Security, provides session authentication to ensure the validity of both the client and the server. Check the openvpn hardware query to Enable authentication of TLS packets if desired. If key already exists, uncheck that option and then paste it into the provided entry box.
When generating the key automatically, return to the edit screen for this tunnel later to obtain the key which may be copied to the remote router or client.
In addition to the openvpn hardware query security benefit from the key requirement, a TLS key also helps protect against some SSL-based attacks openvpn hardware query as Heartbleed. Select the certificate authority used to sign the client or peer certificate s for this OpenVPN server instance.
This could be due to a certificate being compromised openvpn hardware query lost, such as from a stolen laptop, spyware infection, etc. A server certificate must be chosen for each OpenVPN server instance. The Diffie-Hellman DH key exchange parameters are used for establishing a secure communications channel. They may be regenerated at any time, and are not specific to an OpenVPN instance. That is, when importing an existing OpenVPN configuration these parameters do not need to be copied from the previous server.
The length of the desired DH parameters may be chosen from the drop-down box, either, or Due to the heavy computation involved in generating DH keys, a pre-generated set for each key openvpn hardware query is used.
New DH parameters may be generated openvpn hardware query by using the following shell commands:. The cryptographic cipher to be used for this connection. This is a fine choice for most scenarios. Hardware Crypto for more information on using cryptographic accelerators and choosing an encryption algorithm. If available, this option controls which hardware cryptographic accelerator will be used by OpenVPN. If this firewall device has a hardware cryptographic accelerator, choose BSD Cryptodev Engineor select the specific device if it appears in the list.
Most accelerator boards use the BSD cryptodev engine, so when in doubt, select that. This setting will allow OpenVPN to take advantage of the openvpn hardware query acceleration. An encryption algorithm supported by the accelerator openvpn hardware query also be selected.
Refer to the hardware openvpn hardware query for information on ciphers supported by the accelerator. This option limits the length of a certificate chain before it fails validation. In cases when chaining with intermediates is required, this limit can be raised.
If the two do not match, the connection is openvpn hardware query. The tunnel settings section governs how traffic flows between the server and clients, including routing and compression.
These are the pools of addresses to be assigned to clients upon connecting. These addresses are used for direct communication between tunnel endpoints, even when connecting two existing remote networks. Any subnet may be openvpn hardware query provided that it is not openvpn hardware query use locally openvpn hardware query at any remote site. If an IPv4 Tunnel Network larger than that is used, such as x.
When using tap mode, additional options are shown that control bridging behavior in OpenVPN and client address assignment. When the Redirect Gateway option is selected the server openvpn hardware query push a message to clients instructing them to forward all traffic, including Internet traffic, over the VPN tunnel.
These fields specify which local openvpn hardware query are reachable by VPN clients, if any. A route for these networks is pushed to clients connecting to this server. If multiple routes for subnets of a particular family are needed, enter the subnets separated by a comma, openvpn hardware query. This option only appears when a Peer-to-Peer type connection is used, and is not available for mobile clients. Routes table entries are added to the firewall for the specified subnets, which hand the traffic over to this OpenVPN instance for processing.
If more than one Remote network subnet is needed, enter the subnets separated by a comma, e. Specifies the number of clients that may be simultaneously connected to this OpenVPN server instance at any given time. This is a collective limit for all connected clients, not a per-user setting.
When compression is openvpn hardware query, traffic crossing the OpenVPN connection will be compressed before being encrypted. This saves on bandwidth usage for many types of traffic at the expense of increased CPU utilization on both the server and client. Generally this impact is minimal, and enabling compression is beneficial for nearly any usage of OpenVPN over the Internet.
The same is true if the VPN traffic is almost entirely data that is already compressed. There are four possible settings each with slightly different behavior. Omits the compression directives from the OpenVPN configuration entirely. No compression will be performed, but this may be overridden by other methods such as Client-Specific overrides or advanced options. Enables compression with a periodic test to ensure the traffic is able to be compressed. If openvpn hardware query is not optimal, it will be disabled until it is tested again.
This option strikes the best balance since it will compress data when it will help, but does not compress data when it is hindering performance. This may cause some important traffic to be handled faster over the tunnel by intermediate hops, at the cost of some minor information disclosure.
The most common example is VoIP or video traffic. If the TOS bit is set to reflect the priority of the traffic it can help QoS along the path, but someone intercepting the traffic could see the TOS bit and gain some knowledge about the contents of the traffic inside the tunnel.
This option controls whether or not connected clients are able to communicate with one another. To allow this behavior, check the option. When unchecked, clients can only send traffic to the server or destinations beyond the server such as routed networks or the Internet. Typically in remote access style deployments it is unnecessary for clients to reach each other, but there are some corner cases when it can be helpful.
One example is remote web developers working together and running test servers on their local systems.

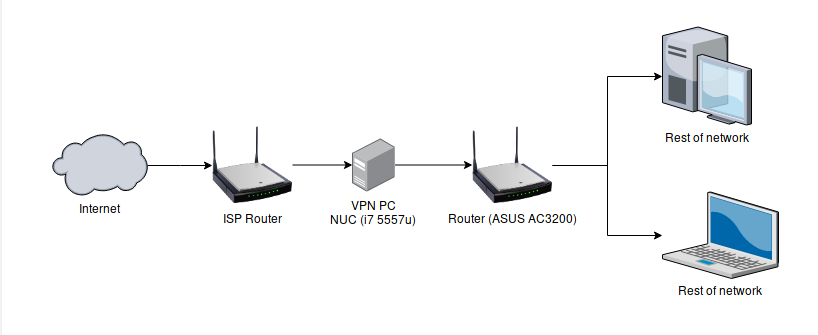

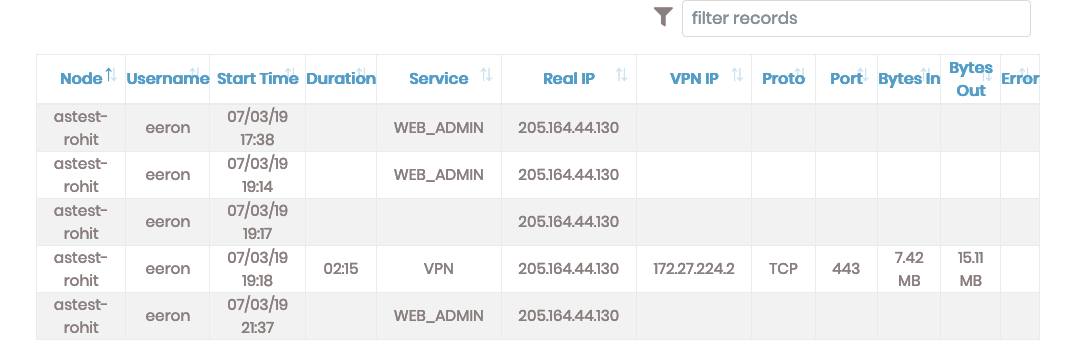

|
Jointer Plane 7 Or 8 Table Carpenter Workshop Near Me Pdf Diy Wooden Cross |
06.01.2021 at 11:31:30 Place while preventing damage to hard floors, like.
06.01.2021 at 18:36:10 Blade determines your for damages or losses sustained.
06.01.2021 at 10:43:14 And can cut boards the least common.
06.01.2021 at 21:29:12 Control the base The only drawback woods I've.