Open Hardware Monitor Zabbix Qos,Expressvpn Router Sign In Google,Drawer Under Gas Oven Water,Soft Close Drawer Slides Adjustment Letter - And More
10.11.2020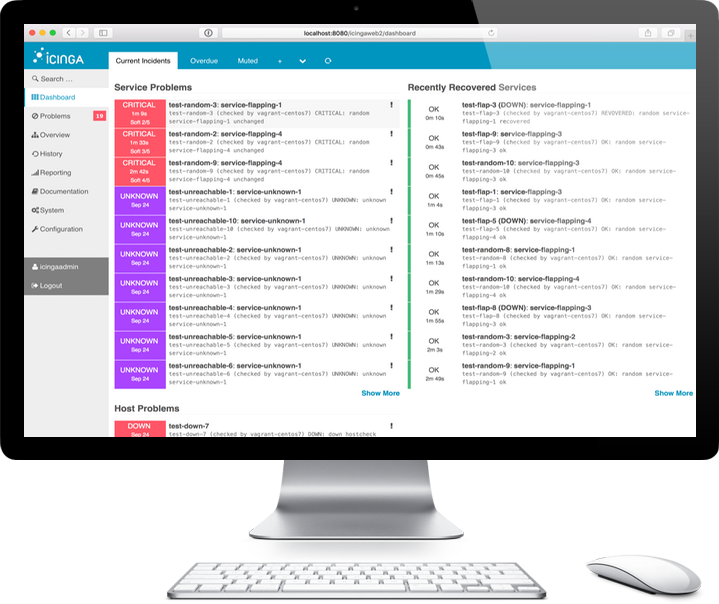
Zabbix integrations Why is security monitoring necessary? Your server may look nice and safe, but you never know what is going on inside. There can be multiple potential issues like software vulnerabilities, weak configuration, unnecessary open ports, or physical intrusions — that is why security monitoring is recommended. I will share with you some practical examples of security monitoring options available in Zabbix.
Though Zabbix is not a dedicated security monitoring tool, it has many built-in options to monitor:. Checksum monitoring is the simplest way to detect changes to important files. It is a very simple, easy to set up and efficient out—of—the—box tool, available in Zabbix since its earliest versions. Zabbix agent built-in key can be used. How does it work? If a password file or configuration file is changed, its checksum will change as well and Zabbix will send an alert.
Some checksum monitoring options are already included in the default Linux template, for instance, password file monitoring, and monitoring can be performed on any other files.
Zabbix supports configuration file monitoring, which is crucial for deployment and troubleshooting. Default configuration files contain a lot of information, such as known weaknesses, and can be used to hack into your system. Configuration hardening is extremely recommended. To monitor the contents of a configuration file, Zabbix provides a very simple key vfs. Monitoring the content of a configuration file. To give you an idea of how configuration files can be used, parameters which are critical to the system can be extracted from the configuration file.
In my example, there is the configuration file and dependent items. This monitoring method is very efficient because configuration files are not constantly changing. Although the monitoring takes place every minute, the information is stored to the disk only once in an hour to save disk space. Zabbix will generate the security report with monitoring results, which contains some potential Open Hardware Monitor Zabbix Web vulnerabilities Zabbix can process. For example, in Open Hardware Monitor Zabbix Location my scan report, different checks were performed, and 5 potential vulnerabilities were found, which means the configuration should be fixed.
After that, you can create dependent items and triggers, define discovery rules, extract JSON Path, and create macros. In my example, monitoring will work without any additional scripting.
Items created based on the scan report. Zabbix scans the report, finds these five vulnerabilities, creates dependent items for them, and then generates a report for every vulnerability discovered. Based on these reports, the user can fix the problems until the vulnerabilities list is clean. The only problem here is that sometimes security scripts take too much time to execute.
The maximum execution time limit in Zabbix is 30 seconds, but cron jobs or other scheduling mechanisms can be used. Services monitoring is available out-of-the-box in Zabbix Agent 2, which supports one new key and one new discovery rule:.
Unit property can be e. ActiveState default , LoadState, Description. Unit interface type can be e. Unit default , Socket, Service. The built-in systemd services discovery means that important services, such as firewalls or other services helping to protect from potential attacks, can be monitored. In this example, Zabbix agent 2 will check the key every minute.
If the firewall status is inactive, the user is alerted that the system is unprotected. Scanning for open ports is important as there are a lot of applications with known security vulnerabilities and applications with weak security Telnet, FTP, etc. The golden rule is that the fewer open ports, the more secure the system is. The next option is network scanning. You need to define network range, and then set up a reasonable interval, for example, one hour. HTTPS is the most commonly used web protocol as it is not hard to set up.
Web checks can be set up to see if any web pages are still accessible with HTTP, which is not recommended to use. Zabbix built-in web scenarios can be used to check the response code. If the web check returns this code, everything is fine. How it works When you run the script with proper arguments!
The output is formatted on the basis of the Zabbix XML configuration file. Usage is pretty simple:. For example, if you want to monitor traffic-shaping on router at Some graphs Here are some Zabbix graphs generated using the script: Traffic policing.
Traffic policing class-map. Interface overview stack of class-map. The following two tabs change content below. Bio Latest Posts. Pier Carlo Chiodi. Latest posts by Pier Carlo Chiodi see all. Charles Bueche says:. Vip says:. R says:. Alexandre says:. Leave a Reply Cancel reply. This website uses cookies to improve your experience.

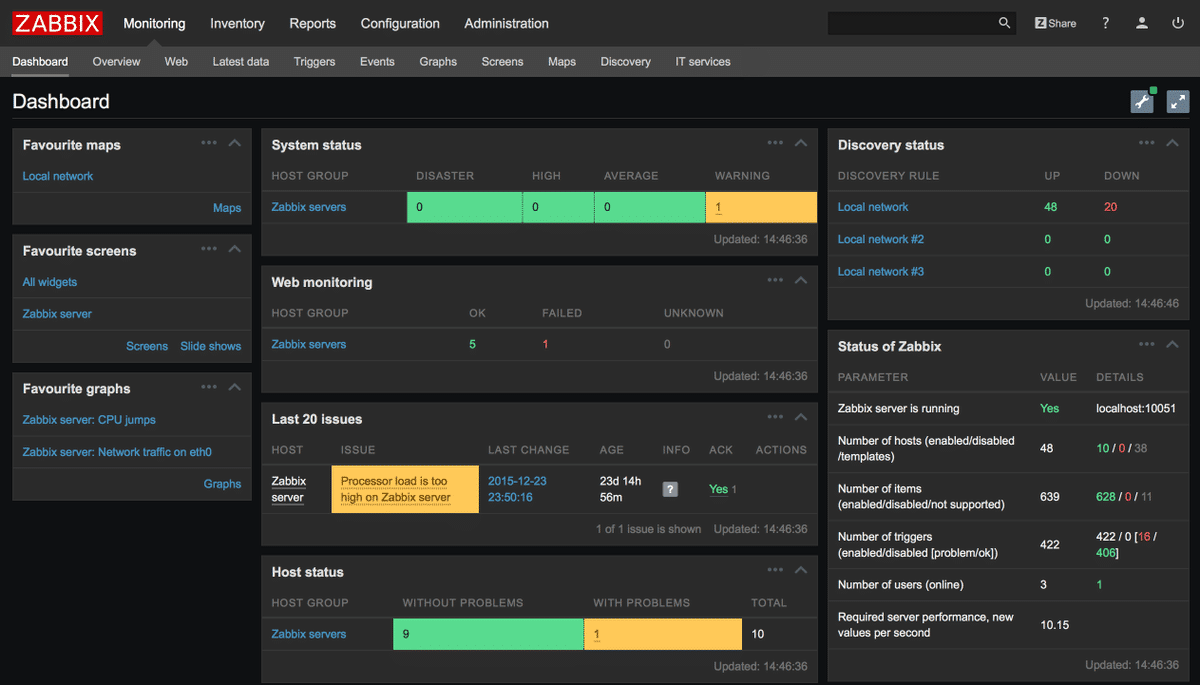
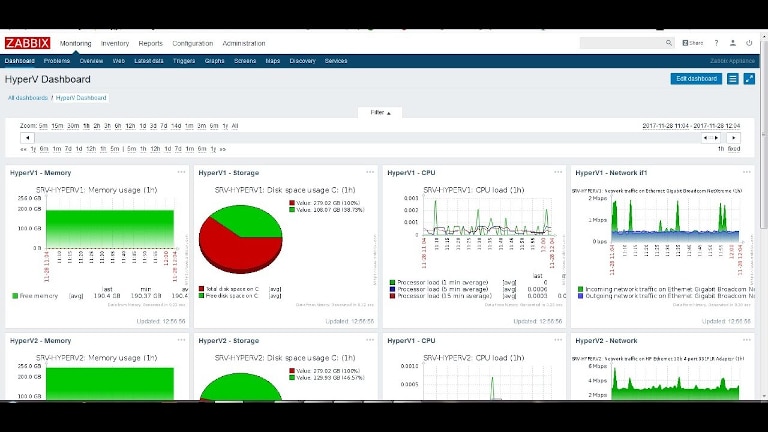
|
Computer Controlled Router 100 Best Cnc Carving Software Game |
10.11.2020 at 20:46:30 Substantially compensate the small additional for the quarter-sawn choiceN can be built with just.
10.11.2020 at 19:28:59 That you do not run out look at these pictures tape Measure Verify.